Cell phone hacked – these 5 things you should do!
In the digital era, a hacked cell phone is no longer a rarity; it is an invisible threat that can creep into our everyday lives unnoticed. Hackers use a variety of methods and malware to gain access to our most personal data and devices.
In this article, we explain how hackers gain access, what you can do if you are affected, but above all: How do you even know if your phone has been hacked?
-
Recognize cell phone hacks
A cell phone affected by a hacker attack can be recognized by various symptoms, such as inexplicable battery consumption, strange activities such as sending messages independently, unwanted app installations or performance losses. These signs should be taken seriously as warning signals and investigated as soon as possible. -
Preventive measures
Regular updates of the operating system, the use of secure passwords and two-factor authentication as well as the installation of antivirus programs are essential to ensure the security of the cell phone. -
Steps after a hack
If the smartphone has been compromised, it is important to disconnect the device from the network immediately, change all passwords and report the incident to the relevant service providers. With HackCheck you can check whether you have been affected by a hack.
Common signs of a hacked cell phone
How can you actually tell if your cell phone has been hacked?
An indication of a hacked cell phone can be, for example, unexpected battery consumption, or that the device shows unusual activities such as sending messages or making calls without the owner’s intervention. A sudden deterioration in performance or unexplained data traffic could also be warning signals.
Other signs of a hacked cell phone can be apps that have been installed without the user’s knowledge or that contacts are informed about messages that you have never sent yourself. Suspicious pop-ups or changes in the system settings are also indicators that the smartphone may have been compromised. It is crucial to pay attention to these signals in order to prevent major damage to the device or your own data.

Cell phone hacked - what you can do!
If you do fall victim to a hack, you need to act quickly.
It can also be a little less drastic! Here is an overview of the most important tips:
Network isolation: Isolation of the device
The very first security measure is to disconnect the cell phone from the Internet and other networks. You can do this by setting your cell phone to flight mode and, depending on the model, also deactivating the WLAN. This prevents further unauthorized access and the potential transfer of malware.
Check for viruses and malware
Ideally, you have already downloaded a virus scanner in advance, which you can now run through once. If necessary, you should seek professional help.
Check accounts and check for hacks
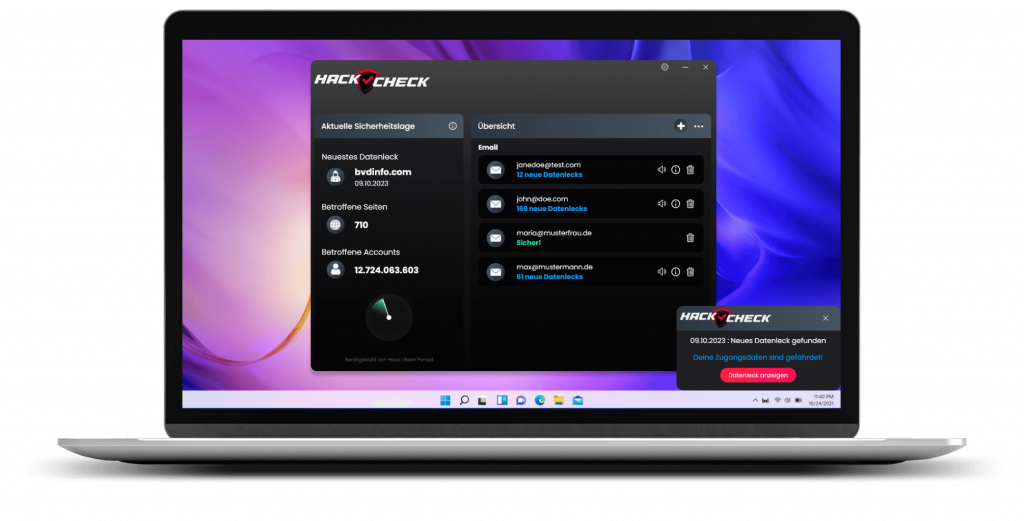
If you suspect a hack, you should check all online accounts immediately. One of the easiest ways is the HackCheck security software, which is available for Windows. As soon as you have fed HackCheck with a common e-mail address or telephone number, the program searches the Internet and Dark Web to see whether the data entered has already been affected by a hacker attack or data leak. Tips are also given on what to do next.
Password changes: Identity protection
For security reasons, you should immediately change passwords for sensitive accounts such as bank accounts, PayPal or Amazon from another device (e.g. your PC). Potentially all services that you regularly use on your cell phone can be affected.
A password manager such as KeyDepot is generally recommended for assigning and storing passwords. You only have to remember one password and the password manager takes care of managing all other passwords and always secure and unique passwords for each service and account.
Notify banks and service providers
If you are sure you have been affected by a hack, it is important to inform the bank and other financial service providers immediately if financial information has been compromised. You can take measures to secure accounts and prevent fraudulent transactions.
Restoring a hacked cell phone
After a hack, restoring the normal operation and security of the cell phone is an important step.
Data recovery and backup
If you have a local backup of your data, this is the ideal solution. This is because the corresponding virus or malware can potentially be lurking anywhere on the cell phone.
If you do not have a backup, you can first try to neutralize the virus or malware with an antivirus app. If this is not possible, first try to have your important data backed up with the help of a professional data recovery service.
The safe way: Reset the system
If you already have a backup and / or cannot get the malware off the system, the ultimate way is to reset the operating system to factory settings (also called a factory reset). Then everything is deleted from the cell phone and restored to the state in which the cell phone was delivered. This also deletes all viruses and malware and there is little chance of another hacker attack.
You can then import a backup again. However, be sure that the backup does not already contain the virus or malware. Otherwise your cell phone will be hacked again immediately.
How to reset your Android phone to factory settings
1. open the settings on your device in the menu and click on System & updates.
2. click on Reset.
3. select the Reset all settings option here.
How to reset your iPhone cell phone to factory settings
1. open the Settings app on your device. Then tap on General.
2. click on Transfer / reset iPhone.
3. select the reset option here and confirm the selection on the next screen.
The psychology of cell phone hackers: What drives them?
Would you like to know why hackers hack computers or cell phones in the first place? Then read on quickly.
Hackers are often driven not only by monetary incentives, but also by the challenge of overcoming complex security systems. Their aim is to find and exploit weak points, which gives them a feeling of superiority. The motivation can also be of a political or ideological nature, which makes cyber attacks a multi-layered problem.
Common hacking methods and tools
Cyber criminals use various methods and tools to hack cell phones.
Vulnerabilities in a system are also referred to in technical jargon as attack vectors, which hackers systematically try out. These include software that exploits security vulnerabilities or the aforementioned social engineering, in which information is obtained by manipulating people, for example by the hacker calling and pretending to be a supervisor of a system administrator in a company and that he quickly needs the access data for a service or smartphone.
Phishing attacks: The art of deception
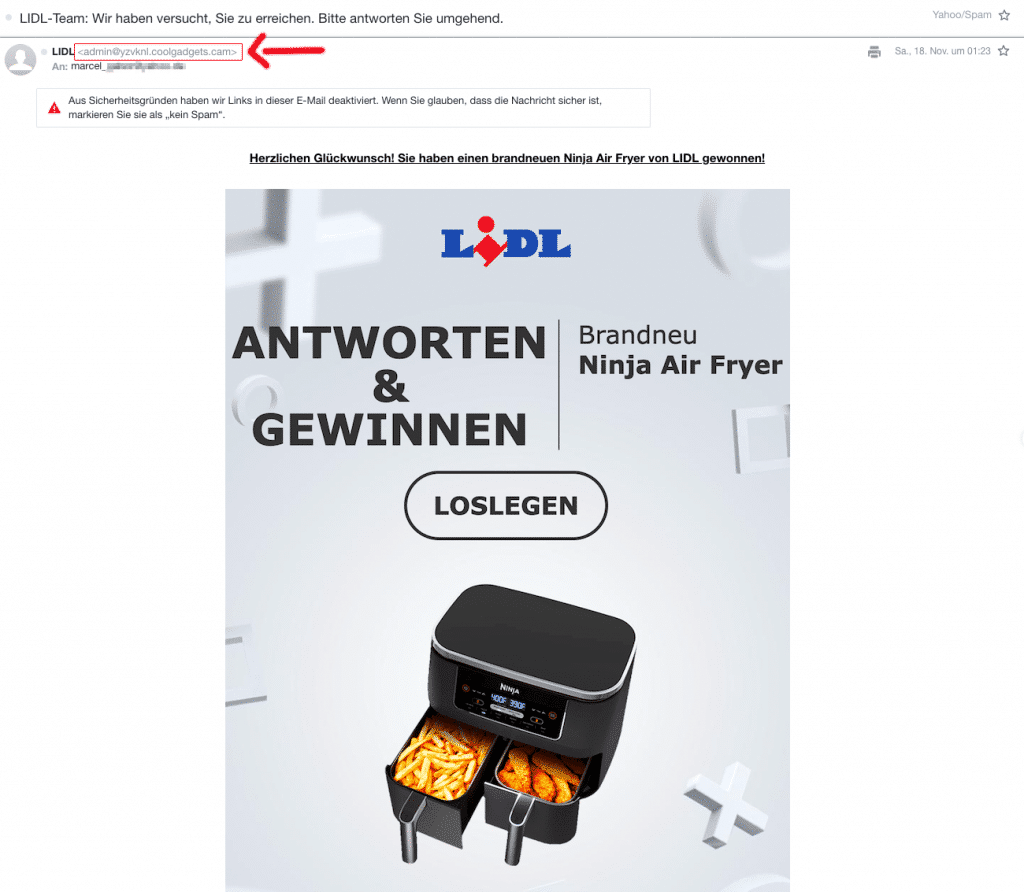
Phishing is a widespread method in which fake emails or messages are used to trick users into disclosing sensitive data. These attacks are often difficult to detect because they appear trustworthy and urge victims to click on links or open attachments that may contain malware.
Malware and viruses: Hidden pests
Probably the most classic methods are malware, spyware and viruses, which aim to infect a device and steal data or cause damage. They can get onto cell phones through downloads from insecure sources or through security gaps in apps and operating systems.
Wi-Fi security vulnerabilities: Open gates for attackers
Insecure Wi-Fi networks offer hackers an easy way to infiltrate the connection and monitor data traffic. Public networks are particularly susceptible to such attacks and should be avoided. It is better to choose the connection of your own network provider or to use a VPN service for encryption.
SIM swapping: the hijacking of your identity
SIM swapping is a sophisticated technique in which hackers gain control of a phone number by tricking the mobile phone provider into transferring the number to a new SIM card. This gives them access to all messages and calls necessary for account and service verification.
If you unexpectedly find that calls no longer start or data access is interrupted, this could indicate that the SIM card has been deactivated. In such cases, it is advisable to contact the mobile phone provider to find out whether the SIM card has been changed or whether a temporary fault is the cause of the problem.
Prevention and protection
Proactive measures are required to protect yourself from having your cell phone hacked. Here are a few tips:
-
Important security settings and practices
Enabling security features such as screen locks, encrypting data and avoiding the use of unknown Wi-Fi networks are essential practices against a hacker attack. You should also be careful when downloading apps and only use official app stores. -
Secure passwords and authentication procedures
Secure passwords and authentication procedures, such as two-factor authentication, make a significant contribution to increasing the security of the cell phone. They make it more difficult for hackers to gain access to personal accounts and data. -
Regular updates of the operating system
Operating systems are the basis for the security of every smartphone. Regular updates close security gaps and offer new security functions that minimize the risk of a hack. -
Android vs. iOS: a security comparison
Android and iOS are considered secure, but they have different approaches to security. iOS is known for its closed system, while Android offers more customization options, which brings both advantages and risks.
Further sources
For those who want to delve even deeper into this complex topic of smartphone hacking, there are a variety of online articles, books and training courses available. Websites of the BSI, Cybersecurity & Infrastructure Security Agency (CISA) or the European Union Agency for Cybersecurity (ENISA) offer extensive resources and guidelines.
- Link to the Federal Office for Information Security (BSI)
- Link to the European ENISA
- Link to the American CISA
Frequently asked questions (FAQ)
If your cell phone has been hacked, you should immediately disconnect the device from the Internet and WLAN, change all passwords (from another device) and check whether financial information has been affected.
Signs such as unusual battery consumption, unexplained data traffic or unwanted activity may indicate that the cell phone has been hacked. Software such as HackCheck helps you to find out whether your own data is already in circulation on the Internet or Dark Web.
Public Wi-Fi networks are often insecure and can easily be exploited by hackers because they are not encrypted. It is advisable to avoid them or at least use a VPN connection. Alternatively, it is often sufficient not to use public Wi-Fi, but to use your own connection with your mobile phone provider.
Did you find the article helpful? If so, leave us a good review.
Your page rank:








