Data breach – You can now test whether you are affected for free
What is a data breach and what can you do if you are affected by one?
This is exactly what we want to explain to you in this article. We’ve also put together some tips to help you protect yourself or what you can do to avert damage quickly. Enjoy reading.
-
What is a data breach?
When private information such as email addresses or credit card details are stolen through a security breach, this is known as a data breach - a digital theft of personal data. -
Consequences of security vulnerabilities
Data leaks can have serious consequences: from unauthorized purchases in the name of others to the opening of accounts, resulting in financial losses and costly clarification processes. -
What you can do
Strong, individual passwords and regular software updates form the basis for data protection. Monitoring tools such as Abelssoft HackCheck are useful to be informed quickly if your data is affected by a data leak.
What is a data breach?
Generally speaking, a data breach is an incident in which confidential data is retrieved or made accessible from a protected system or medium without authorization. The data concerned may be personal information such as names, addresses, telephone numbers, e-mail addresses, credit card numbers or health data. This can also include business data such as customer data, employee data or trade secrets.
The term “data breach” is usually used synonymously with the term “data leak”. The term “data security incident” is used in legislation and companies are required to report it.
Types of data breaches
Data breaches can be divided into different categories based on the type of incident:
- Physical data breaches: Include the loss or theft of physical documents or devices, such as laptops or cell phones, that contain sensitive information.
- Electronic data breaches: This refers to unauthorized access to electronic systems, whether through hacking, ransomware or other malware.
- Unintentional data breaches: These occur when information is accidentally released or published, often due to human error.
- Deliberate data breaches: These occur through targeted attacks on data systems, often by cybercriminals or angry insiders acting for profit or revenge.
Personal consequences of data breaches

Data breaches or data leaks are not only a violation of privacy, but also entail specific risks. One of the most common direct results is identity theft, where personal data is misused to commit fraud. This can take the form of illegally opened accounts, credit card fraud or forged identity documents and often leads to lengthy and complicated processes of damage limitation and recovery.
Many people often use the same combination of e-mail address and password. If this data is part of a data leak, criminals can use this data to attempt to log on to various online services such as eBay, Amazon and others in the name of the victim. Even if most online services have now set up good security barriers, there is still a residual risk.
In addition to the direct material damage, the psychological impact should not be underestimated. The feeling of being exploited and hurt, accompanied by worries about your own financial and personal security, can lead to a state of persistent anxiety and stress.
What to do in the event of a data breach?
An effective tool in the fight against the consequences of data breaches is the Windows program
Abelssoft HackCheck. This security software represents a modern monitoring system and informs users immediately if their online accounts, telephone numbers, e-mail addresses or passwords are affected by a data leak. The program searches the Internet and Darknet around the clock. It searches for indications of data leaks and security breaches and compares these with the data provided by the user.
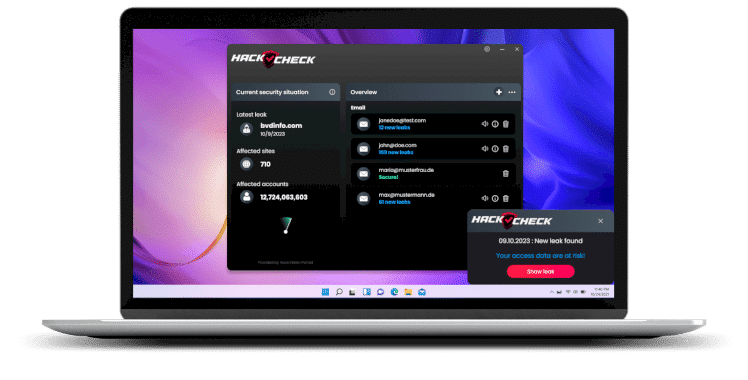
As soon as a potential risk is identified, HackCheck notifies the user, provides details on the scope of the leak and gives recommendations on how best to respond, such as changing passwords or contacting affected services. This enables those affected to act quickly to restore their digital security and minimize potential damage.
Many data subjects are surprised when they see which data is already in circulation and which data breaches have already affected them.
Prevention and protective measures against data breaches
Password management: secure passwords and multi-factor authentication
Data encryption for the individual: A personal protective shield
The encryption of personal data is also very important for individuals. Encryption is an effective means of preventing unauthorized access, both for data stored on your own device and for information that is transmitted online. Private individuals should pay attention to end-to-end encryption when using messenger services such as Whatsapp or Signal. Hard disk encryption on laptops and external storage media also protects against data access in the event of theft or loss of the device.
Regular security updates: patching vulnerabilities
Software and security updates are crucial for closing known vulnerabilities and keeping systems up to date. Companies and authorities should ensure that all systems, applications and devices are regularly updated to provide protection against the latest threats.
Be careful when shopping online: secure payment options and secure websites
When shopping online, it is important to only shop on secure websites and use secure payment methods. Users should look for HTTPS in the browser address bar and verify the authenticity of the website before entering any personal or financial information. The use of credit cards or secure payment services can offer additional protection.
Social networks: be careful with personal information and privacy settings
On social networks, users should carefully consider what information they share and who can see it. Adjusting privacy settings to only share information with trusted contacts and being aware of phishing attempts are important measures to protect data on social media.
Cloud services: Use of reputable providers and data encryption
When using cloud services, users should choose providers that are known for their security measures. Data stored in the cloud should be encrypted and users should regularly check who has access to their data. Here too, it is important to use strong passwords and multi-factor authentication. In recent years, Apple has been particularly committed to data protection and has particularly high standards with its iCloud and similar services.
Summary: Important findings for private individuals to protect against data breaches
Data breaches put personal data at risk and can lead to identity theft and financial loss. Private individuals should take proactive protective measures: Use of strong passwords, multi-factor authentication and regular updates are essential. Tools such as Abelssoft HackCheck can help to detect security breaches at an early stage. Careful handling of authorizations and the use of secure cloud services are additional important steps in maintaining digital security.
Further sources
For those who want to delve even deeper into this complex topic, there are a variety of online articles, books and training courses available. Websites of the BSI, Cybersecurity & Infrastructure Security Agency (CISA) or the European Union Agency for Cybersecurity (ENISA) offer extensive resources and guidelines.
- Link to the Federal Office for Information Security (BSI)
- Link to the European ENISA
- Link to the American CISA
Frequently asked questions (FAQ)
The term “data breach” is usually used synonymously with the term “data leak”. As a rule, this means that private data such as bank details, e-mail address, credit card details or more have been stolen from a company where they are stored.
The term “data security incident” is used in legislation. A data security incident is an event that results in the unintentional or unlawful access, disclosure, alteration, destruction or destruction of personal data.
If you are affected by a data breach, you have the following rights:
- You have the right to be informed by the company that caused the data breach. The company must inform you of the type of data affected, the number of persons affected and the measures taken to rectify the incident.
- You have the right to receive free support from the company that caused the data breach. This support may include, for example, paying credit reference agencies, monitoring your credit score or paying for identity theft recovery costs.
- You have the right to take legal action against the company that caused the data breach.
If you have been the victim of a data breach, you should take the following measures:
- Change your passwords for all accounts that could be affected by the data breach.
- Check your bank accounts and credit cards and report any unauthorized transactions.
- Order a free copy of your credit report.
- Inform your credit card companies about the incident if you suspect that credit card data or similar has been affected by the data leak.
- If you suspect that your identity has been stolen, you should also contact the police.
Did you find the article helpful? If so, leave us a good review.
Your page rank:








